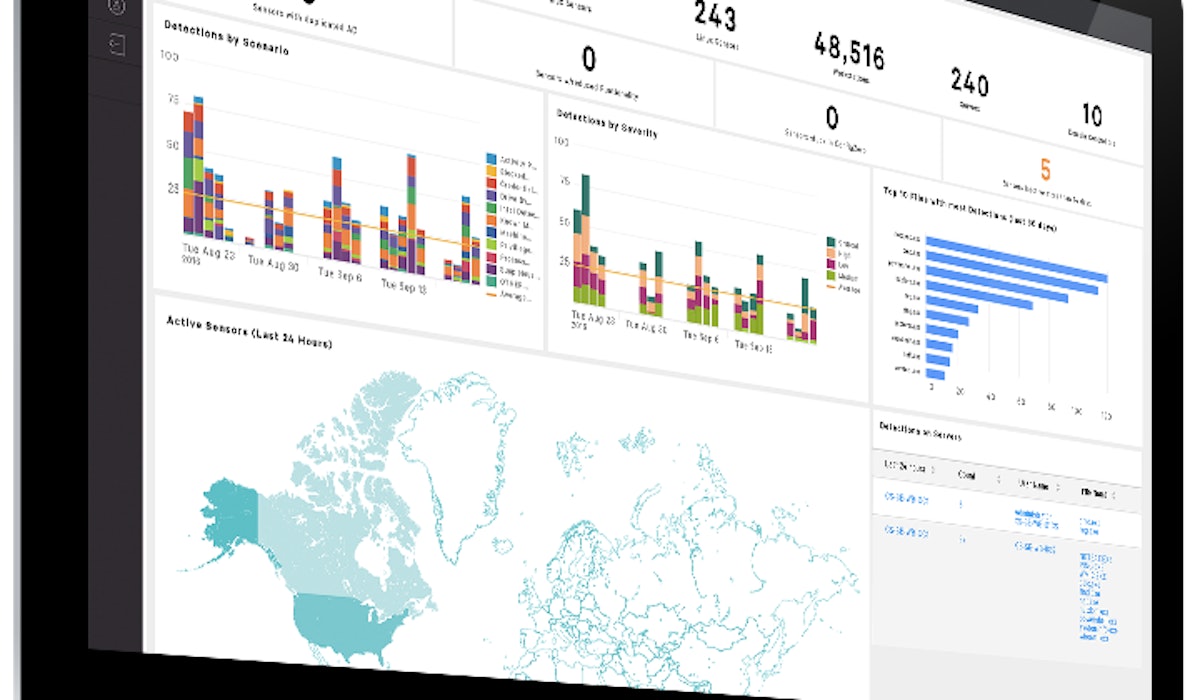
Setting the new standard in endpoint protection
The CrowdStrike Falcon® platform is pioneering cloud-delivered endpoint protection. It both delivers and unifies IT Hygiene, next-generation antivirus, Endpoint Detection and Response (EDR), managed threat hunting, and threat intelligence - all delivered via a single lightweight agent. Using its purpose-built cloud-native architecture, the Falcon platform collects and analyses more than 30 billion endpoint events per day from millions of sensors deployed across 176 countries.
The Falcon agent (small and light) and cloud (big and powerful) work seamlessly to deliver real-time protection and visibility -- yes, even when the agent is not connected to the internet. The simplicity of CrowdStrike’s architecture finally gives you the freedom to replace and retire the complicated, performance-robbing security layers that clutter your environment.
Stop breaches
With unified endpoint protection delivered from the cloud
The Falcon Platform is flexible and extensible when it comes to meeting your endpoint security needs. You can purchase the bundles or any of the modules listed below. The additional modules can be added to Falcon Endpoint Protection bundles.
Stand-alone modules can be purchased by anyone and do not require a Falcon Endpoint Protection bundle. Our specialised products are for customers working with more stringent compliance or operational requirements.
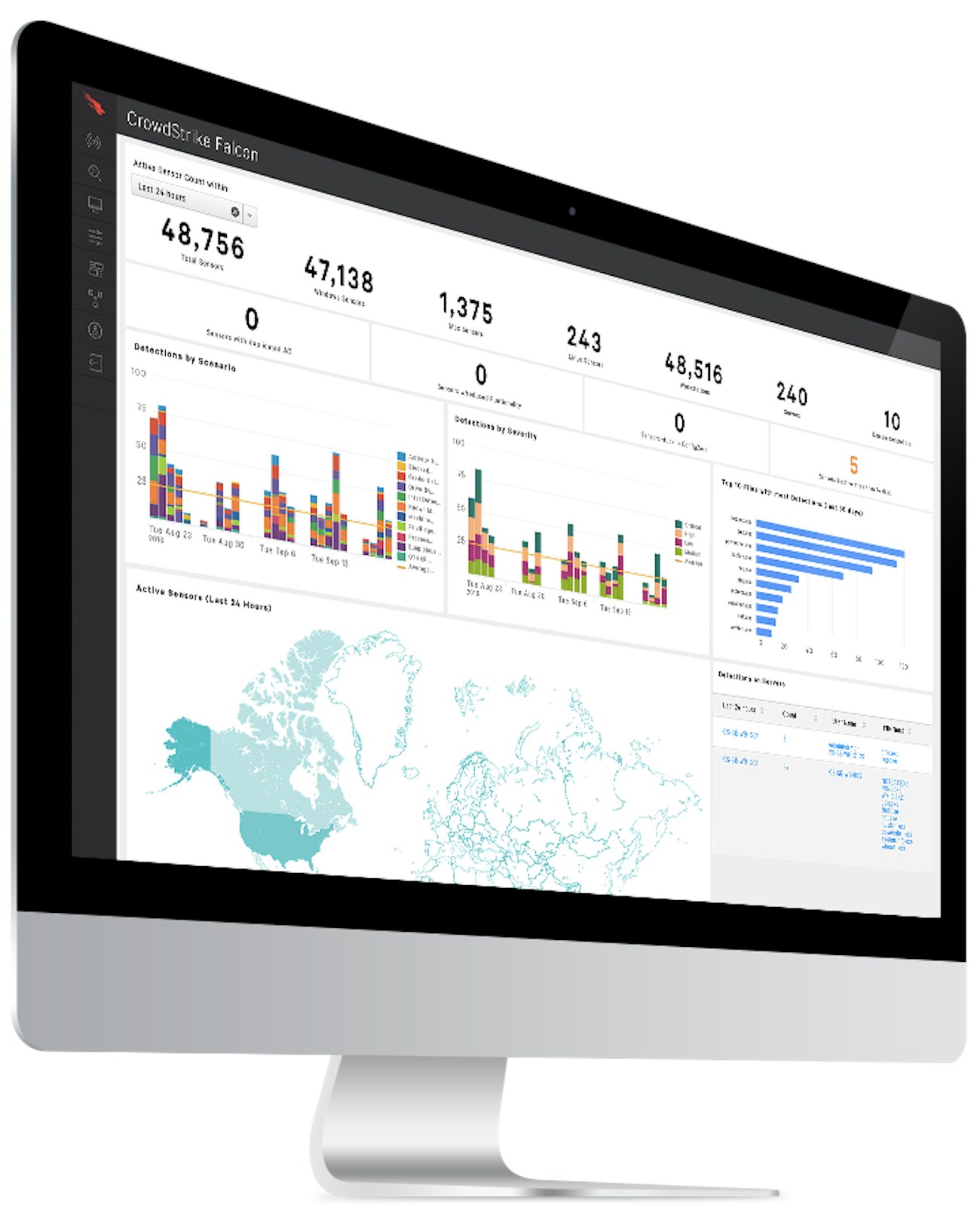
Why CrowdStrike Falcon?
- Better protection
- Prevention and detection against all attack types- both malware and malware free
- Immediate time to value
- Cloud architecture reduces cost while adding speed, efficacy and scalability
- Better performance
- Consolidates a full range of security functionality into one integrated solution
- Cloud-native next-generation antivirus
- Up and running immediately
CrowdStrike Falcon bundles

Falcon Pro
Market-leading NGAV is proven to stop malware with integrated threat intelligence and immediate response - with a single lightweight agent that operates without the need for constant signature updates, on-premises management infrastructure or complex integrations, making it fast and easy to replace your AV.
- Falcon Prevent
- Falcon X threat intelligence
- Falcon device control: USB device control
- Falcon firewall management, host firewall control

Falcon Enterprise
Unifies the technologies required to successfully stop breaches, including true next-gen antivirus and Endpoint Detection and Response (EDR), managed threat hunting, and threat intelligence automation, delivered via a single lightweight agent.
- Falcon Prevent, next-generation antivirus
- Falcon X, threat intelligence
- Falcon device control, USB device control
- Falcon firewall management, host firewall control
- Falcon Insight, EDR
- Falcon Overwatch, threat hunting

Falcon Elite
Take breach-stopping power to the next level with integrated endpoint and identity protection, expanded visibility, and elite threat-hunting.
- Falcon Prevent, next-generation antivirus
- Falcon Intelligence, Threat intelligence
- Falcon device control, USB device control
- Falcon firewall management, host firewall control
- Falcon Insight XDR, Detection & response for endpoint & beyond
- Falcon Overwatch, threat hunting
- Falcon Discover, IT hygiene

Falcon Complete
Endpoint protection delivered as-a-service and backed with a breach prevention warranty up to $1M.
- Falcon Prevent, next-generation antivirus
- Falcon X, threat intelligence
- Falcon device control, USB device control
- Falcon firewall management, host firewall control
- Falcon Insight, EDR
- Falcon Overwatch, threat hunting
- Falcon Discover, IT hygiene
Ready to talk?
Are you looking for pricing details, technical information, support or a custom quote? Our team of experts in Brussels is ready to assist you.